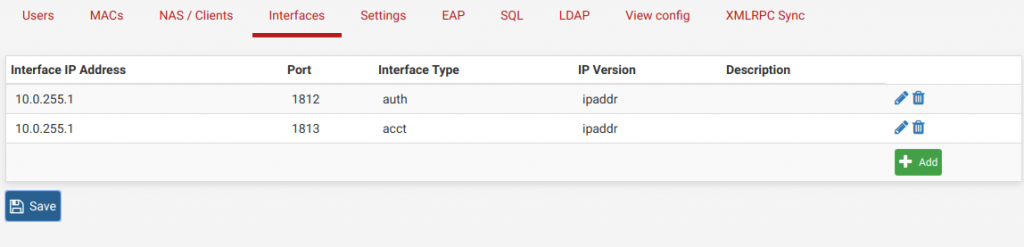
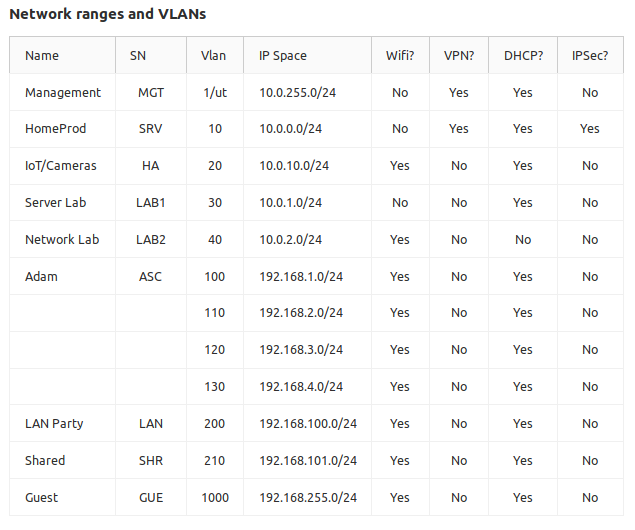
I’ve never done real, actual wire fishing before. I’ve pulled stuff in a straight line through walls, I’ve done drop ceilings and such, but this was a new challenge for me – 16 ports to start, 4 rooms, plus the attic for 2 Unifi access points, through a finished basement.
So naturally the first thing I did was pull out my studfinder and poke a hole in the wall of my computer room. When fishing wire there are a couple things you don’t want to find: Insulation, PVC pipe, water damage, bug damage… So go figure I find the first 2 on the first hole.

Luckily I now have a landmark. So I took some measurements upstairs and went downstairs, plotted out my spot on the ceiling, and made a big ol hole, which revealed the PVC pipe. Score. Took my spade bit and drilled a hole some inches to the right, then went and got my fishtape.

The joists in the house run perpendicular to the ventilation and the support beam that runs the length of it. From the furnace room I could see there was a 12″ x 12″ void space that runs the entire length of the house that’s also perpendicular to the joists. That’s where I planned to run the cable, since at most it was only a couple right-angle turns and I’d be right there.
Next up I started running the cable down into the hole I’ve made.

I got these 2 spools of Monoprice Cat6a and threw them on my weight rack. They hold the weight while allowing the spools to spin freely, plus now I’m actually getting some use out of the thing.
I pulled a good 20 feet down through the hole, then immediately went over to the next room and cut another ceiling-hole. Threw the fishtape over and pulled it, and I’m now sitting right at the void space. Perfect.

The void space is fun because it’s encased in a blocked-out area of the finished basement. That means a lot of horizontal 2×4’s, and I found that fishtape is a lot more useful when gravity is your friend. So I went out and got some fiberglass fish poles. Less flex, more ability to get them over the 2×4’s.
I made a giant hole in the middle of the ceiling. Hooray. If there was a point before where I could turn back, I’ve surely blown straight past it now.
I threw some Ideal fish line into the hole, threw a hook on the end of my pole, put it down to the end and swished it around. I still can’t believe this worked. It’s about a 20 foot run.

So using this I created a fish guide. I was going to have to do a couple more pulls and I didn’t want to have to fish it again.


From down here it’s just a quick turn, up and over the ventilation to the server room. Cue another hole in the ceiling, one I care much less about the shape of because it’s going to get a custom shroud eventually.

To end out the day, I pulled another 2 from that room, and 4 more from the bedroom next to it since it’s right above hole number 2. I didn’t have to cut any additional drywall for that one so it’s a huge plus.
Next day I got the wallmount rack set up…

…and the first 4 ports wired.

Stellar. Really chugging along now.
For the next bit, I figured some torture would be great. I’m terribly afraid of heights. The only access to the attic is in my fairly tall garage. I have a ladder, but it’s about 2 feet short to make a comfortable ascent. So why not get the Unifi AP cables run.
I don’t have any pictures of this since I forgot my phone before going up there, but wading through 2 feet of blow-in insulation is now my idea of the worst way to spend an afternoon.
Fortunately, this run is from the only unfinished room in the basement, and my house is a ranch, so it was a fairly easy pull to go straight up using the radon exhause pipe as a landmark. 8 inches to the north from the basement, 8 inches to the north from the attic, and bam, straight shot. Pulled the run, terminated, got the fuck outta the attic, line tested with my laptop, and I’m a happy camper.

This run was a 4-cable run. 2 went to the attic, 2 to the office, which has the wall where I ran the cables up.
Nearing the end. 12 lines run. Now it’s just the living room left to do. Usual procedure, popped open the wall, used my 3 foot flex bit to make it easier. Fished this one with the help of my wife, who has been very patient with me through this whole thing and I appreciate the hell out of her for it.



Easy peasy, doesn’t look half bad for an amateur.
The network cabinet is starting to look pretty solid here.
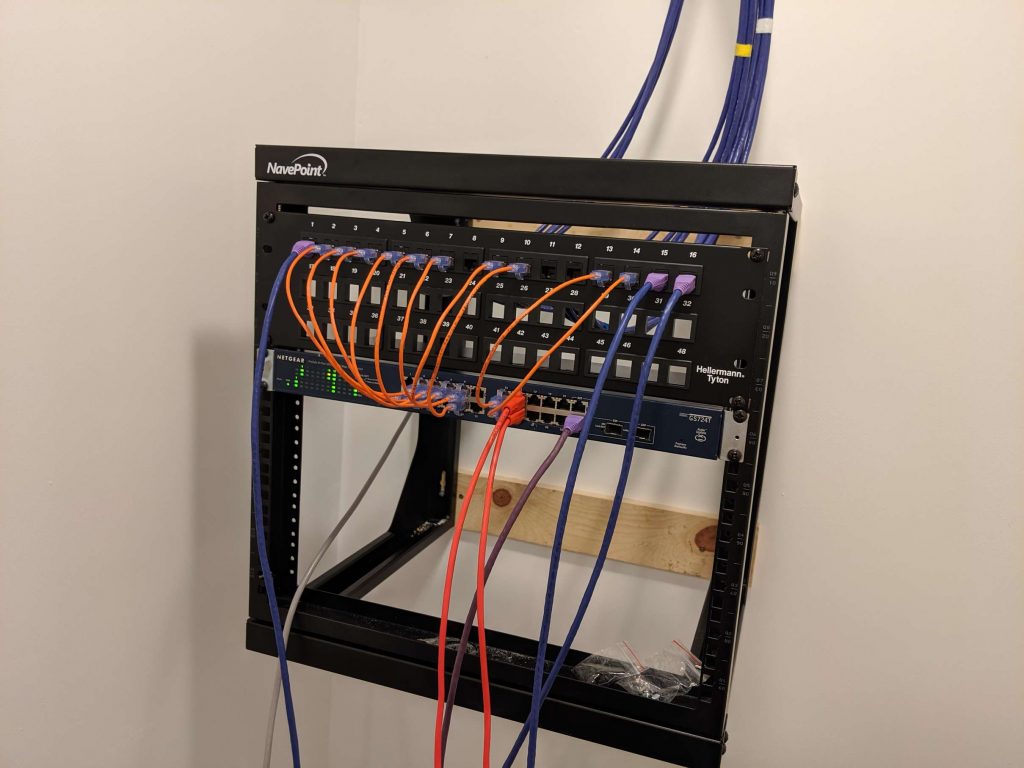
Then to wrap it all up I did some more cable management in the computer room, since the jacks are on the opposite side as the PC’s.

Now I’m sitting here at the end of my little 5-day project and feeling a lot more confident about doing the same thing in the basement. Shooting for sometime in October for the next expansion, which will put me in a good spot if we end up hosting our annual Thanksgiving lan party.
Next up: Couple Cisco fanless switches are on order and should be here in the next week. Those will take the place of my Netgear, which is slightly too loud for the room.